Dummy’s Guide to Cybersecurity

Cyber Security can be an overwhelming topic for anyone who has just started to research about this terminology.
However, it is as simple as “The method that secures computer and mobile devices, network, vital information, from data theft, misuse or attack on the system.”
Cyber Security is a subset of network security, which focuses on protecting the infrastructure, internal data, and information. It also manages access control, roles, firewalls, and passwords.
Operational Security
Operational security determines the ways to protect organizational assets and follows the following modus-operandi:
- Identify Assets
- Find threats
- Determine the vulnerabilities
- Assess associated risks
- Take countermeasures
Application Security
Application security focuses on building a reliable security feature into the services and applications provided to the internet.
Information Security
Information security follows a framework of processes policies and provides tools that secure data and information from any kind of misuse and attack.
Disaster recovery and Business revamp
This module focuses on the recovery after a cyberattack and security events, including the plans required for the recovery of assets, as well as business continuity.
Why is Cybersecurity important in today’s world?
There are more than 2.7 Billion mobile phones, 3 Billion+ desktops, and everything around us is getting digitized from finances, clothes and grocery shopping, appliances, travel, as well as dating and getting married. Wherever there is an interchange of media or information, cybersecurity plays a vital role to keep devices and servers confidential and secured.
Cybersecurity protects billions of devices and monitors suspicious activities to ensure you get your right weather report, your business transactions are successful, as well as traffic signals changing the lights at the right time for efficient traffic management. A single conspiracy in the system can affect millions of users on a day-to-day basis.
The adoption and integration of disruptive technologies are entering our homes, workplaces, public infrastructure, as well as our washrooms. Hackers get a wide array of opportunities to destroy, disrupt, and trespass the network.
Report suggests that in 2018, 945 data breaches led to a staggering 4.5 billion data records being compromised worldwide. This makes hacking a lucrative job for hackers, which has a substantial income but also pertains to a high level of risks associated with it. The world is going digital with respect to shopping and finances, which provides a perfect time for hackers to invade networks full of credit card information about people.
Roughly 31 percent of consumer transactions were reported to be in the form of digital methods in the year 2018.
Life cycle of a Cyber Attack
Technology has advanced fourfold, and so has the attacking strategies for hackers. Today’s cyberattack strategies focus on patience, multi-step processes that lead to long-term damage, and a coordinated network attack. This all can start by luring a user to click a malicious link and gain root access to the user’s computer. The malware focuses on attaining control inside the network so that the attacker can expand its roots and infect the whole network.
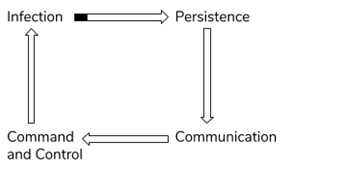
- Infection
- Persistence
- Communication
- Command and Control
1. Infection
An infection is getting a user to click on suspicious links which can be on a social networking site, phishing email, or a webpage infected with malicious images. Most hackers target systems to infect with malware/ spyware and follow the four-step process:
- Phishing/Malware
- Rootkits/Bootkits
- Encryption(SSL,SSH)
- Common Apps (Email, Social Media, P2P)
Once the attacker attains the shell access, it can deliver any kind of load and exploit the target network. An infection can be wrapped in any package according to the user’s taste, behavior, and preferences.
2. Persistence
Once the user’s machine is infected, the hacker needs to ensure persistence. In such a scenario, rootkits and boot kits are installed, the latter one is a kernel-mode variant and is commonly used to attack completely encrypted computers.
This provides a backdoor to bypass authentication processes and gain access to the infected computer.
3. Communication
Attackers communicate with the infected system to enable command & control and extract the desired stolen data from a target network. Keeping the communication private is necessary, and therefore, such techniques are used:
- Encryption
By using SSL and SSH, hackers make their communication secure and communicate with the infected computer with command and control.
- Fast Flux
Fast Flux is also known as dynamic DNS. It helps the infected host to reroute traffic and make it a difficult task for security and forensic teams to figure out where the traffic is going.
4. Command and control
Command and control is the topmost layer of the communication platform that provides the attackers to remain controllable, manageable, and updatable. Command and control are accomplished through applications like webmail, P2P network, financial websites, social media, and forums. Command and control traffic doesn’t raise any kind of suspicion and is well encrypted as it mostly uses backdoors and proxies to enter into the network.
Xpetize Technology Solutions is an IoT solution provider. We also offer Cybersecurity services. Please feel free to contact us to know more about our services.




Leave a Reply